ZWall.net Documentation
Complete guide for the Next-Generation eBPF/XDP Firewall System
System Overview
ZWall.net is an enterprise-grade network security solution that leverages eBPF/XDP technology for high-performance packet filtering and centralized management. The system provides real-time threat detection, distributed enforcement, and comprehensive monitoring capabilities.
🚀 High Performance
eBPF/XDP technology delivers sub-microsecond latency and 10+ Gbps throughput with minimal CPU overhead.
🎯 Centralized Management
Manage thousands of agents from a single web interface with real-time policy synchronization.
🔍 Real-time Monitoring
Comprehensive observability with live traffic analysis, security events, and performance metrics.
🛡️ Enterprise Security
Advanced authentication, audit logging, and compliance features for enterprise environments.
- • IPv4/IPv6 packet filtering with CIDR support
- • TCP/UDP port-based access control
- • MAC address filtering and BPDU protection
- • Rate limiting and DDoS mitigation
- • Real-time security event streaming
- • RESTful API for automation and integration
Project Overview
Project Structure
📁 Root Directory
🔧 Build & Development
⚙️ Configuration Files
📊 Database Schema
Technology Stack
🔥 eBPF/XDP Engine
High-performance packet processing
- • eBPF programs in C
- • XDP for ingress filtering
- • Traffic Control (TC) for egress
- • cilium/ebpf Go library
- • Kernel 4.18+ support
🐹 Go Backend
Concurrent and efficient services
- • Go 1.19+ runtime
- • Gin web framework
- • GORM ORM
- • JWT authentication
- • Concurrent processing
🐘 PostgreSQL Database
ACID-compliant data storage
- • PostgreSQL 12+
- • Connection pooling
- • Advanced indexing
- • JSONB for flexible data
- • ACID transactions
🌐 Web Interface
Modern responsive UI
- • Vue.js 3 framework
- • Tailwind CSS
- • RESTful API integration
- • Real-time dashboards
- • Mobile responsive
🔒 Security Features
Enterprise-grade security
- • TLS 1.3 encryption
- • JWT token authentication
- • Role-based access control
- • Audit logging
- • Secure agent registration
📦 Build System
Automated compilation and deployment
- • GNU Make build system
- • clang/LLVM for eBPF
- • Go build tools
- • Systemd integration
- • Automated testing
Component Descriptions
Manager Service
Central control and management
- • Web interface serving
- • REST API endpoints
- • Agent orchestration
- • Policy management
- • Security event aggregation
- • Database operations
Agent Service
Distributed enforcement
- • eBPF program loading
- • Rule enforcement
- • Event collection
- • Health monitoring
- • Manager communication
- • Local logging
eBPF Programs
Kernel-level packet processing
- • XDP ingress filtering
- • TC egress filtering
- • Real-time rule updates
- • Performance monitoring
- • Event generation
- • Memory-efficient maps
Web Interface
User management console
- • Dashboard views
- • Rule configuration
- • Agent monitoring
- • Security event display
- • System settings
- • User management
Development Workflow
Deployment Environments
Development
Staging
Production
Docker
Key Dependencies
- Linux Kernel: 4.18+ with eBPF and XDP support
- clang/LLVM: 9.0+ for eBPF compilation
- libbpf: eBPF library for userspace interaction
- PostgreSQL: 12+ with PostGIS extension
- systemd: Service management and process supervision
- OpenSSL: TLS certificate generation and validation
- gin-gonic/gin: HTTP web framework
- cilium/ebpf: eBPF program loading and management
- lib/pq: PostgreSQL database driver
- dgrijalva/jwt-go: JWT token handling
- gorilla/websocket: Real-time communication
- spf13/viper: Configuration management
System Architecture
Core Components
Manager (Central Control)
Web interface, API server, policy management, and agent orchestration
Agents (Distributed Enforcement)
eBPF program execution, local monitoring, and event forwarding
Database (Persistent Storage)
Configuration, policies, security logs, and audit trails
Technology Stack
eBPF/XDP Engine
Kernel-level packet processing with zero-copy performance
Go Backend
Concurrent processing, efficient memory management
PostgreSQL Database
ACID compliance, advanced querying, and indexing
Data Flow Architecture
Policy Creation: Web UI → Manager API → Database → Agent Sync
Packet Processing: Network Packet → XDP Hook → eBPF Program → Decision (Pass/Drop)
Event Reporting: Agent → Security Event → Manager → Database → Web UI
Monitoring: Agent Metrics → Manager → Real-time Dashboard Updates
Installation Guide
- • Linux kernel 5.4+ with eBPF support
- • Root privileges for eBPF operations
- • PostgreSQL 12+ for the database
- • Go 1.19+ for building from source
- • 4GB RAM minimum (8GB recommended)
Quick Start
- Clone the repository and navigate to the project directory
- Install system dependencies
- Configure the database
- Build and install the Manager
- Configure and start the Manager service
- Deploy and configure Agents
- Access the web interface
Automated Installation with Scripts
Interactive Setup Script (setup.sh)
The setup.sh script provides an interactive installation process with multiple deployment modes.
🏢 Full System Installation
Complete deployment with Manager, Web Panel, Agent, and Database
🎯 Core Only Installation
Manager and Web Panel without local Agent
🤖 Agent Only Installation
Connect to external Manager
🔧 Development Setup
Development environment with build tools
Setup Script Features
- • System dependency detection and installation
- • PostgreSQL database setup and configuration
- • Go programming language installation
- • Project compilation and building
- • Systemd service creation and configuration
- • TLS certificate generation (Let's Encrypt or self-signed)
- • Authentication setup and admin user creation
- • Network interface detection and configuration
- • Production fixes application
eBPF Activation Script (enable-ebpf.sh)
The enable-ebpf.sh script activates full eBPF protection with all security features.
- • Stops existing services safely
- • Cleans up old eBPF programs and maps
- • Compiles production-ready eBPF programs
- • Loads programs onto network interfaces
- • Verifies protection is active
- • Provides real-time status monitoring
Management and Rebuild Scripts
Manager Rebuild (rebuild-manager.sh)
Rebuilds the Manager service after configuration changes or code updates.
Agent Rebuild (rebuild-agent-only.sh)
Rebuilds the Agent service with updated configuration and eBPF programs.
System Status (system-status.sh)
Comprehensive system health check and status monitoring.
eBPF Monitoring (ebpf_monitor.sh)
Real-time monitoring of eBPF programs and firewall activity.
eBPF Testing (test_ebpf.sh)
Comprehensive testing of eBPF firewall functionality.
Manager Setup
Configuration
The Manager requires configuration for database connection, server settings, and security parameters.
Service Management
Agent Setup
Agent Registration
Agents must be pre-registered with the Manager before deployment for secure authentication.
Verification
Firewall Components
eBPF/XDP Engine
Kernel-level packet processing with sub-microsecond latency
- • XDP ingress filtering at driver level
- • Zero-copy packet processing
- • 14.88 Mpps processing rate
- • Minimal CPU overhead (<5%)
Traffic Control (TC)
Egress filtering and traffic shaping
- • Outbound packet filtering
- • Bandwidth rate limiting
- • QoS policy enforcement
- • Traffic prioritization
Rule Engine
Flexible policy evaluation system
- • IPv4/IPv6 address filtering
- • TCP/UDP port control
- • MAC address policies
- • Protocol-specific rules
Security Features
Advanced threat detection and mitigation
- • BPDU attack prevention
- • Rate limiting and DDoS protection
- • Port scan detection
- • Behavioral analysis
eBPF Program Structure
eBPF Technical Documentation
Core eBPF Programs
firewall.c (XDP Ingress)
Main firewall program for ingress traffic filtering
firewall_egress.c (TC Egress)
Egress traffic filtering and broadcast control
firewall_simple.c
Minimal firewall for basic protection
eBPF Maps Structure
Security Event Types
Layer 2 Threats
- • EVENT_BPDU_BLOCKED (1)
- • EVENT_MAC_SPOOF (2)
- • EVENT_BROADCAST_BLOCKED (11)
Network Scanning
- • EVENT_PORT_SCAN (3)
- • EVENT_PORT_SCAN_OUTBOUND (106)
IP/Port Filtering
- • EVENT_IP_BLOCKED (4)
- • EVENT_PORT_BLOCKED (5)
- • EVENT_PROTOCOL_BLOCKED (6)
DDoS Protection
- • EVENT_SYN_FLOOD (7)
- • EVENT_ICMP_FLOOD (8)
- • EVENT_RATE_LIMIT_EXCEEDED (10)
DHCP Security
- • EVENT_DHCP_BLOCKED (9)
- • EVENT_DHCP_UNAUTHORIZED (13)
VM Security
- • EVENT_VM_ISOLATION (12)
- • EVENT_VM_TRAFFIC_DETECTED (17)
eBPF Program Compilation
Performance Characteristics
- • Latency: Sub-microsecond packet processing
- • Throughput: 14.88 million packets per second (Mpps)
- • CPU Overhead: Less than 5% for full protection
- • Memory Usage: ~2-4MB per interface
- • Map Lookups: O(1) hash table operations
- • Event Rate: Up to 1000 events/second sustained
- • Zero Copy: Direct NIC to userspace data transfer
eBPF Program Loading Process
Installation Guide
Automated Installation with setup.sh
- • Linux distribution (Ubuntu 18.04+, CentOS 7+, AlmaLinux 8+)
- • Root or sudo privileges
- • Internet connection for package downloads
- • At least 2GB RAM, 10GB disk space
- • Go 1.19+ (will be installed if missing)
- • PostgreSQL 12+ (will be installed if missing)
Deployment Modes
Full System Installation
Complete firewall system with manager and agent
Installs: PostgreSQL, Go, Manager, Agent, eBPF programs, Web UI
Core Only Installation
Manager and database only (no agent)
Installs: PostgreSQL, Go, Manager, Web UI
Agent Only Installation
Agent component only (requires existing manager)
Installs: Go, Agent, eBPF programs
Development Installation
Development environment with all components
Installs: All components with debug options
Installation Process
Configuration Files Created
Manager Configuration
Agent Configuration
Systemd Services
Database Setup
Post-Installation Steps
Troubleshooting Installation
- • Permission denied: Run with sudo or as root
- • Package installation fails: Check internet connection and package manager
- • Go compilation fails: Ensure Go 1.19+ is installed correctly
- • Database connection fails: Verify PostgreSQL is running and accessible
- • eBPF loading fails: Check kernel version (4.18+) and BTF support
Web Panel Usage
Dashboard Overview
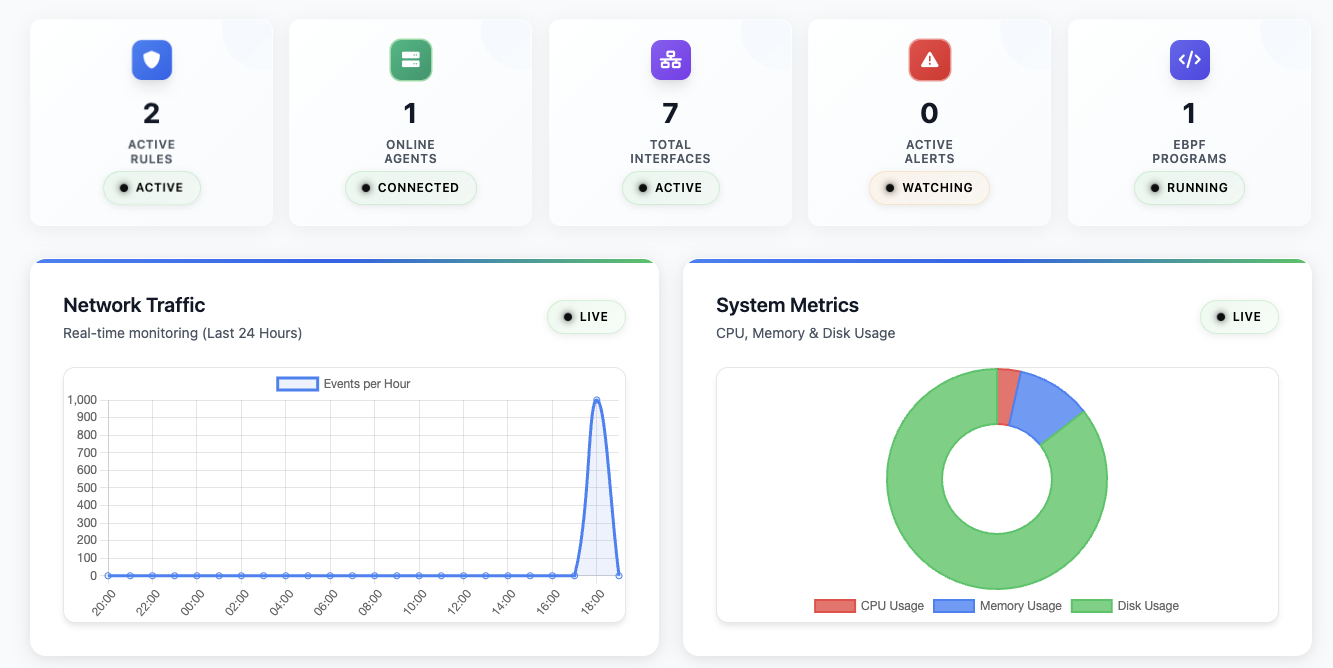
The main dashboard provides real-time visibility into system health, security events, and network traffic.
Firewall Rules Management
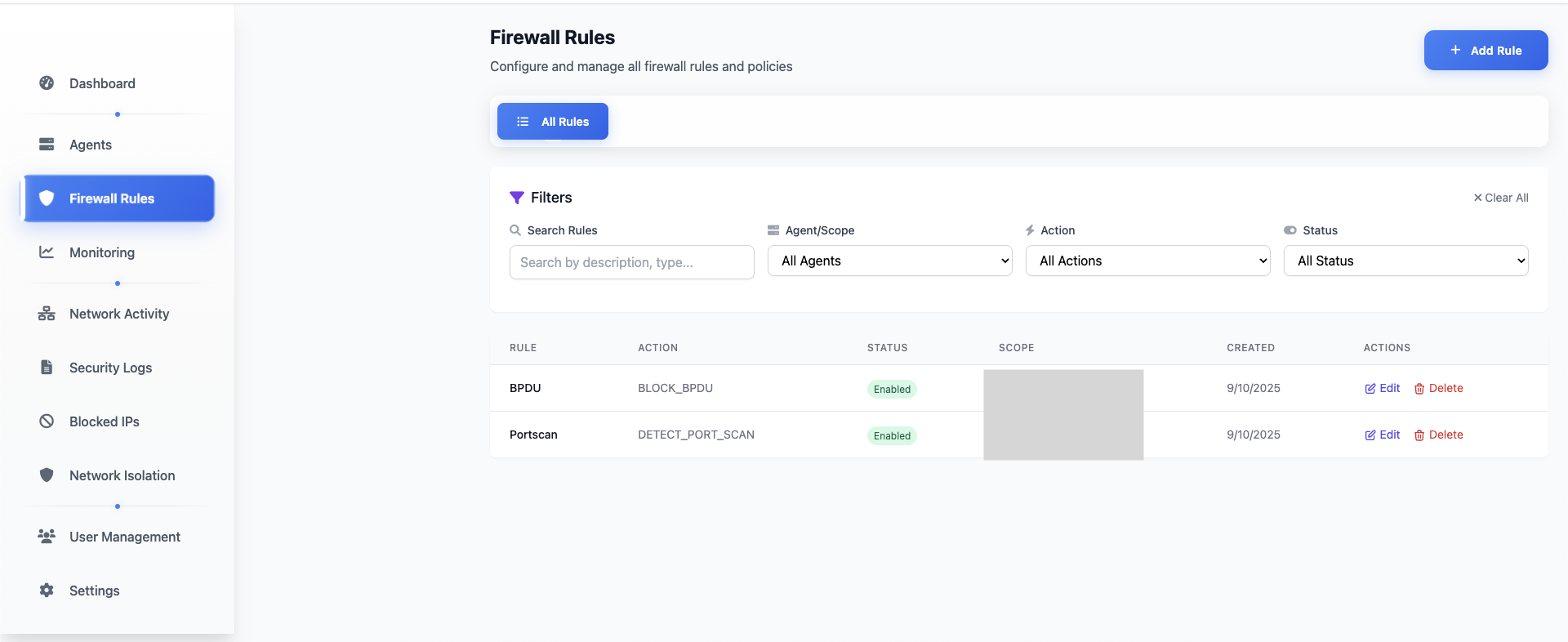
Comprehensive rule management interface with drag-and-drop configuration.
Rule Creation
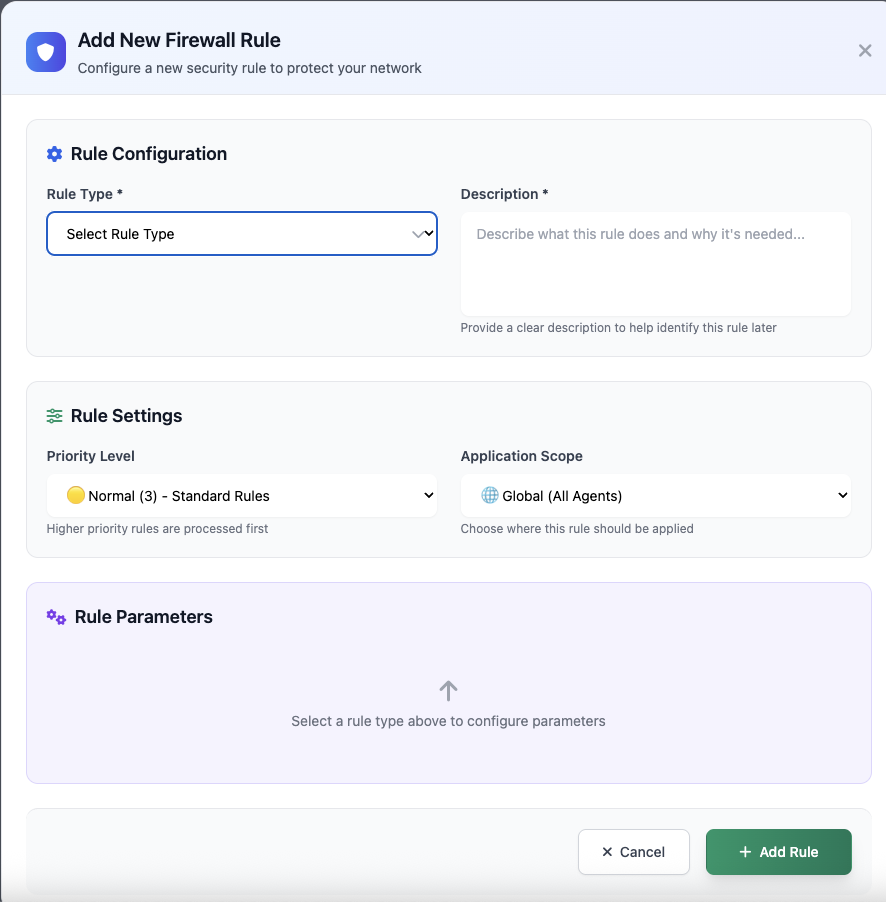
Intuitive rule builder with validation and testing capabilities.
Rule Types
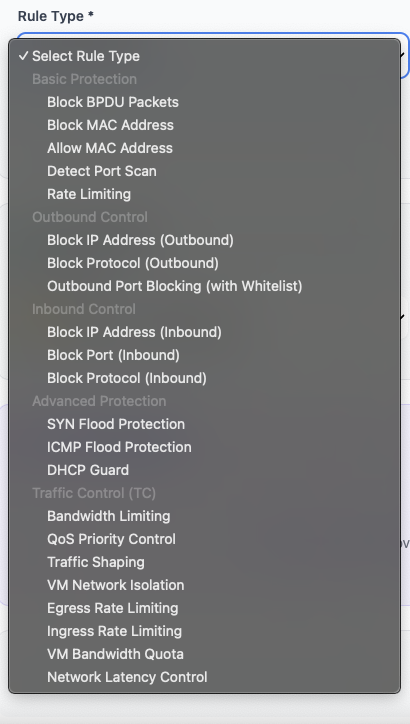
Support for various rule types including IP, port, and protocol filtering.
Agent Management
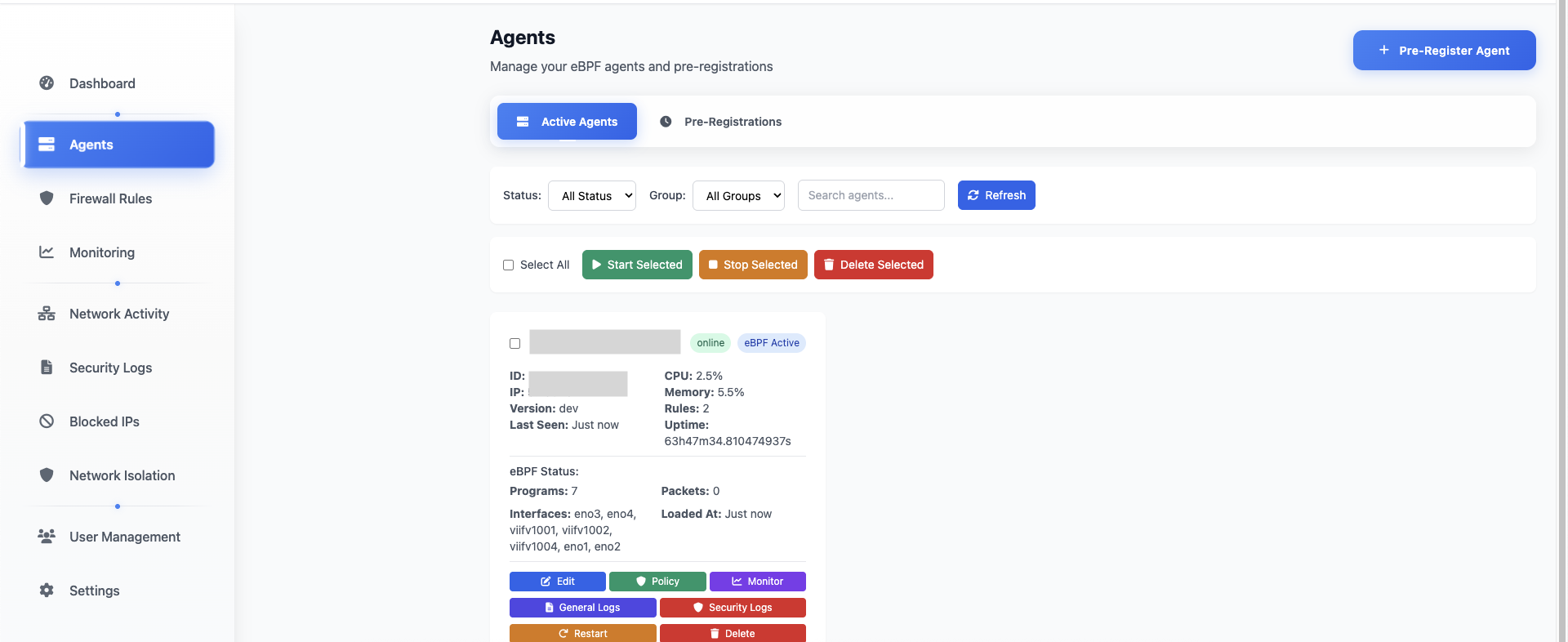
Monitor and control all deployed agents from a centralized interface.
Agent Monitoring
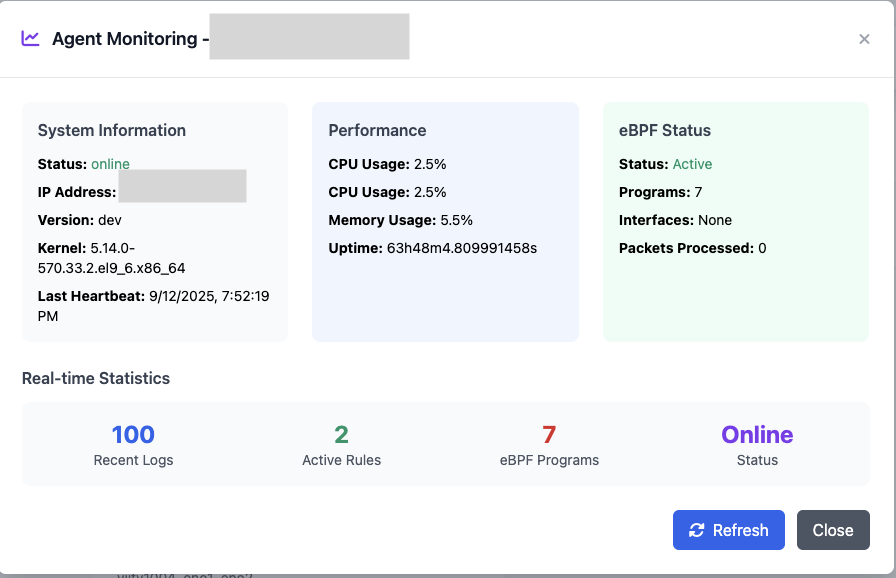
Real-time agent health monitoring and performance metrics.
Pre-registration
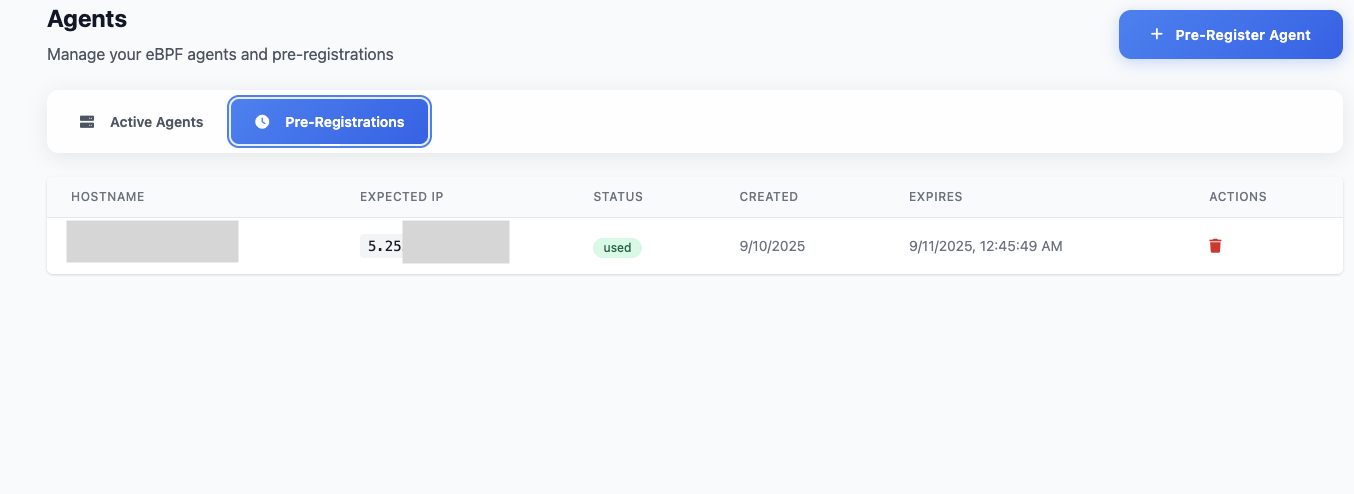
Secure agent registration system with token-based authentication.
Database Schema & Usage
Core Tables
Rules Table
Agents Table
Security Logs Table
Agent Rules Table
Database Operations
System Workflow
Rule Lifecycle
- Rule Creation: Administrator creates firewall rule via web interface
- Validation: Manager validates rule parameters and syntax
- Storage: Rule stored in database with metadata
- Distribution: Rule synchronized to relevant agents
- Application: Agent loads rule into eBPF maps
- Enforcement: eBPF program applies rule to network packets
- Monitoring: Security events logged and forwarded to manager
- Reporting: Events displayed in web interface and stored for analysis
Packet Processing Flow
Agent Synchronization
API Reference
Authentication
Firewall Rules API
GET /api/v1/rules
List all firewall rules with filtering options
POST /api/v1/rules
Create a new firewall rule
PUT /api/v1/rules/{id}
Update an existing rule
DELETE /api/v1/rules/{id}
Delete a firewall rule
Agent Management API
GET /api/v1/agents
List all registered agents
POST /api/v1/agents/register
Register a new agent
GET /api/v1/agents/{id}/status
Get agent health status
POST /api/v1/agents/deploy
Deploy rules to specific agents
Security Events API
GET /api/v1/events
Retrieve security events
GET /api/v1/events/stats
Get event statistics
POST /api/v1/events/export
Export events to CSV
System Management API
GET /api/v1/health
System health check
GET /api/v1/config
Get system configuration
POST /api/v1/config/reload
Reload system configuration
GET /api/v1/logs
Retrieve system logs
Configuration Files
Manager Configuration
Agent Configuration
Error Codes
- 400 Bad Request: Invalid request parameters or malformed JSON
- 401 Unauthorized: Missing or invalid authentication token
- 403 Forbidden: Insufficient permissions for the operation
- 404 Not Found: Resource or endpoint does not exist
- 409 Conflict: Resource already exists or state conflict
- 422 Unprocessable Entity: Validation errors in request data
- 429 Too Many Requests: Rate limit exceeded
- 500 Internal Server Error: Server-side processing error
- 503 Service Unavailable: Service temporarily unavailable
Rate Limiting
Monitoring & Security Events
Security Logs
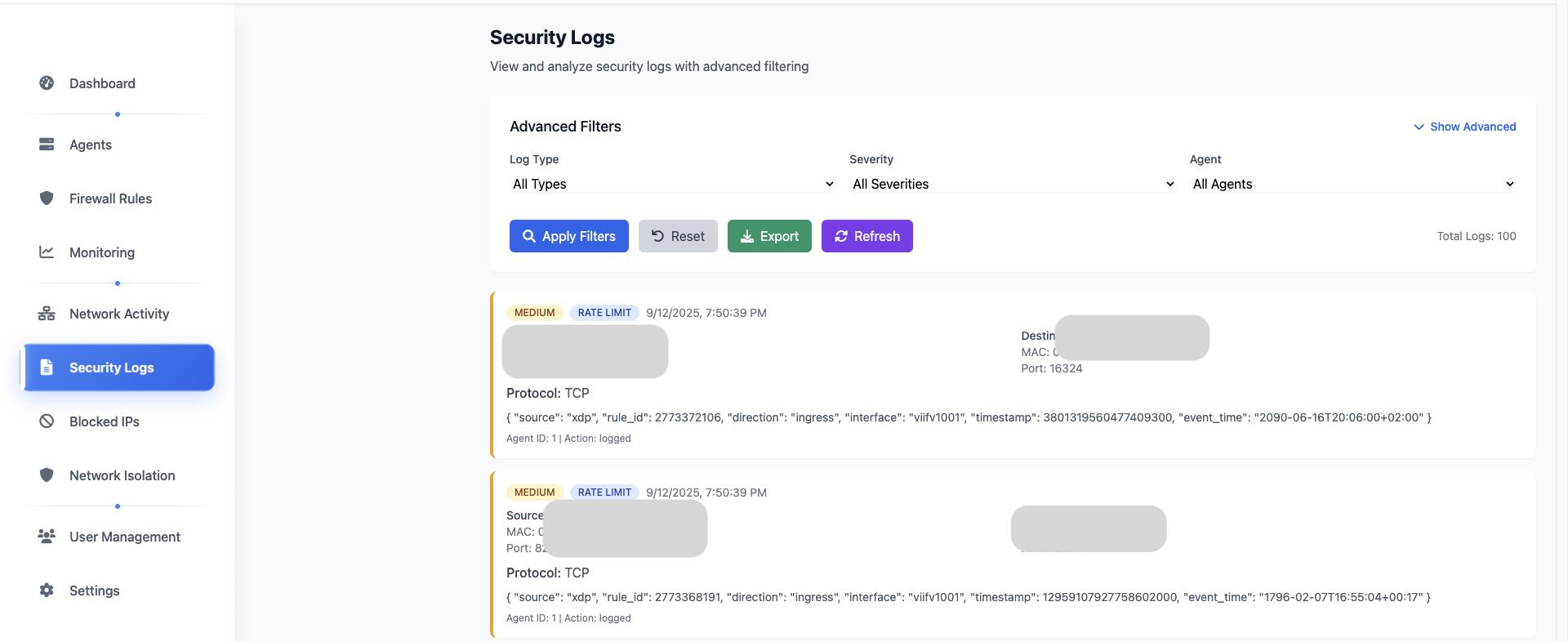
Comprehensive security event logging with real-time streaming and historical analysis.
Blocked IPs Management
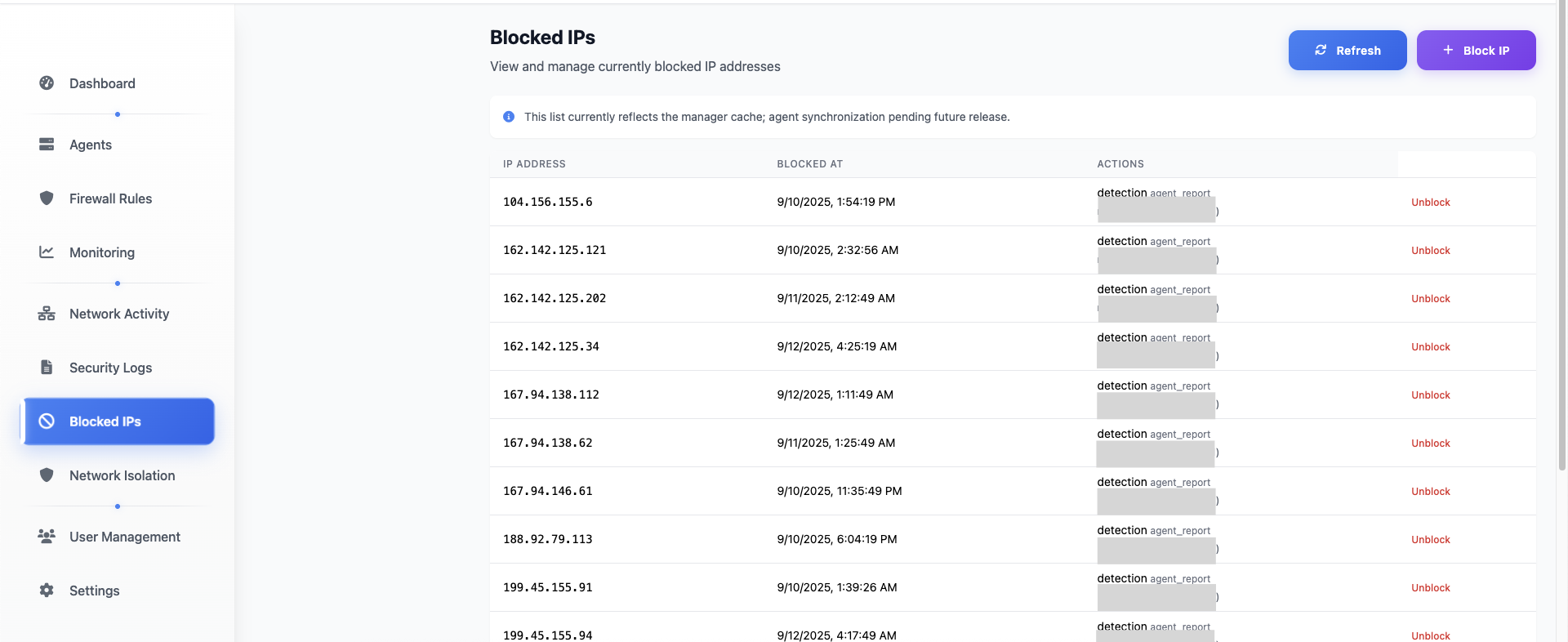
Monitor and manage blocked IP addresses with automatic threat intelligence integration.
Network Isolation
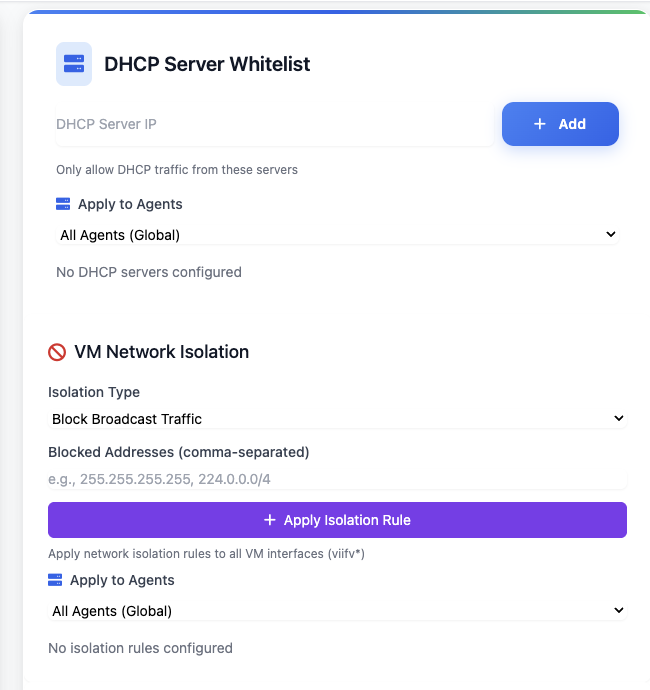
DHCP service control for network access management.
Broadcast Control
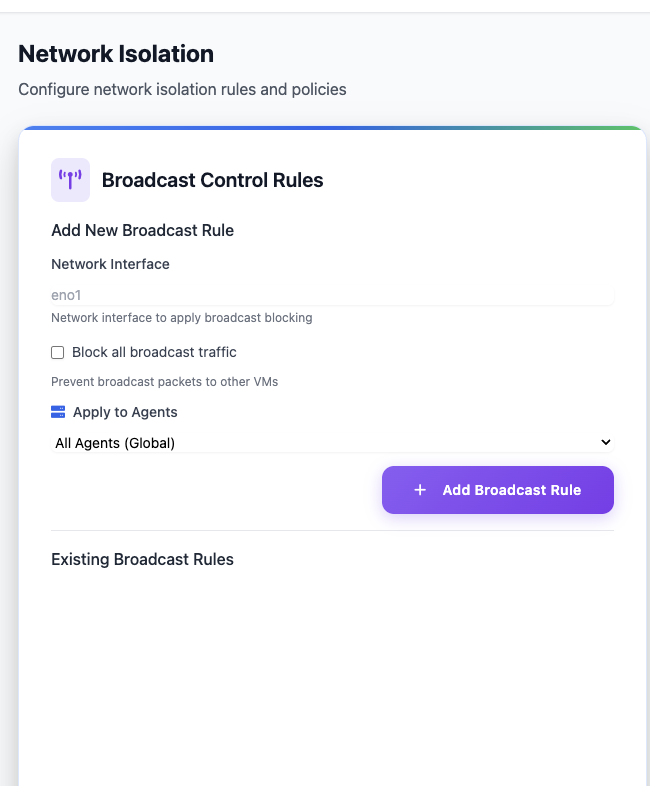
Broadcast traffic management to prevent network storms.
Port Scan Detection
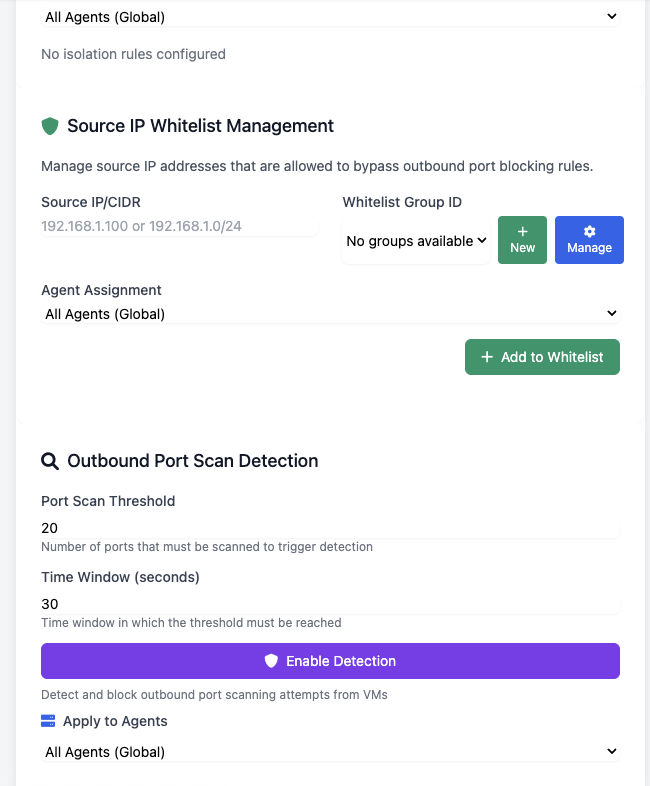
Advanced port scanning detection with whitelist support.
Manager Logs
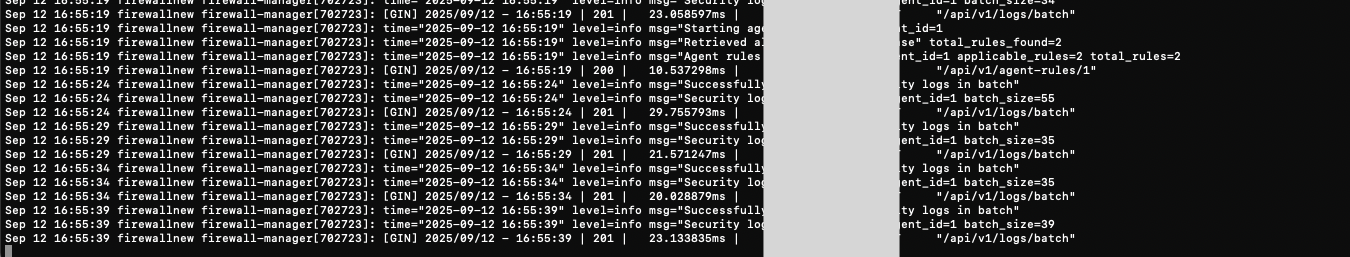
Comprehensive manager activity logging and audit trails.
Agent Shell Access
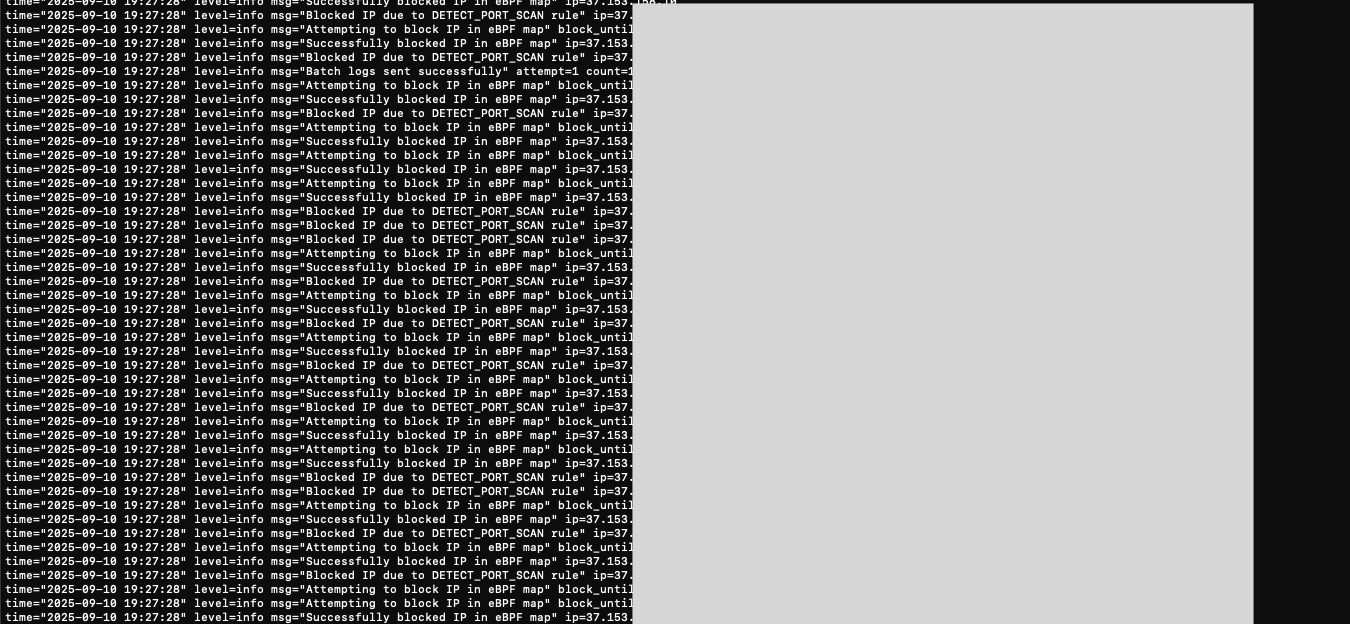
Secure remote shell access to agents for advanced troubleshooting and maintenance.
Settings Panel
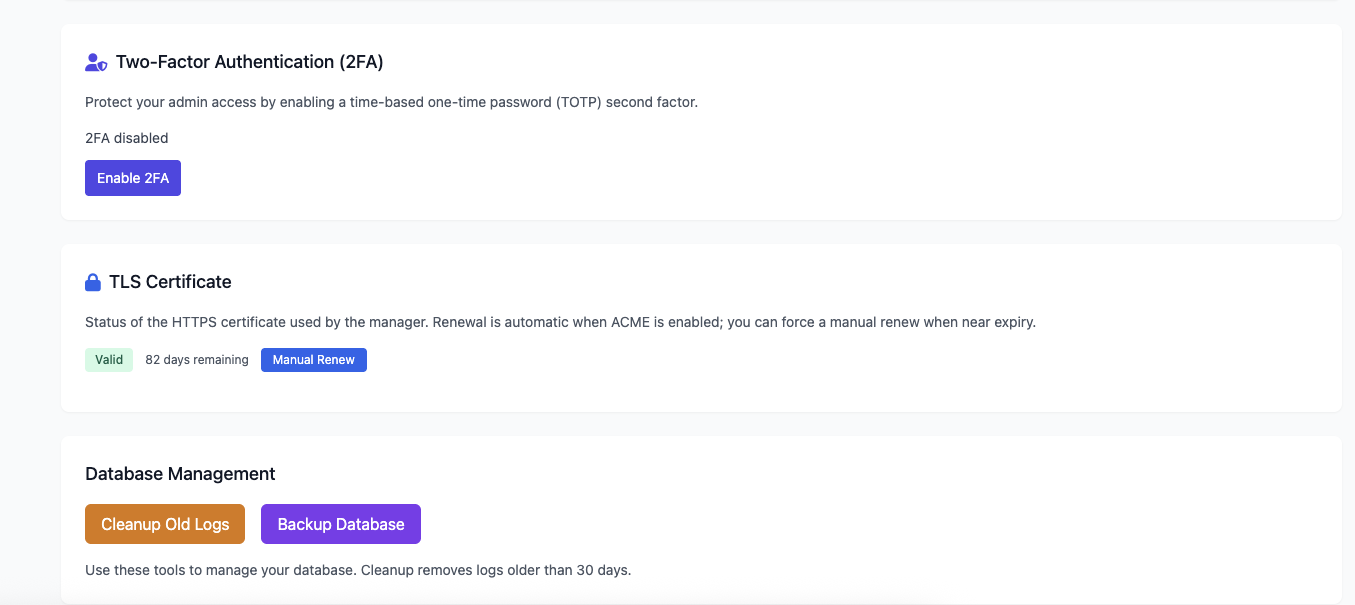
System configuration and settings management interface.
Troubleshooting
System Status Monitoring
- • Service status verification (Manager, Agent, Database)
- • Network connectivity testing
- • eBPF program loading verification
- • Configuration file validation
- • API endpoint testing
- • Recent activity logs analysis
- • Health score calculation
- • Automated recommendations
eBPF Monitoring and Diagnostics
ebpf_monitor.sh Commands
test_ebpf.sh Testing
Common Issues
eBPF Program Loading Failed
Agent Connection Failed
Database Connection Issues
High CPU Usage
Service Startup Issues
Network Interface Issues
Performance Tuning
- • Increase eBPF map sizes for high-traffic environments
- • Use connection pooling for database operations
- • Implement log rotation to prevent disk space issues
- • Configure appropriate rate limiting thresholds
- • Monitor memory usage and adjust cache sizes
- • Use multiple CPU cores for parallel processing
- • Optimize eBPF program complexity for better performance
Log Analysis
Rebuild and Recovery Procedures
Manager Rebuild
Agent Rebuild
eBPF Rebuild
Emergency Procedures
- • Stop all services:
sudo systemctl stop firewall-manager firewall-agent - • Unload eBPF programs:
sudo ip link set dev eth0 xdpgeneric off - • Clear eBPF maps:
sudo rm -rf /sys/fs/bpf/* - • Reset database:
sudo ./scripts/setup.sh --reset-db - • Clean rebuild:
sudo ./scripts/setup.sh --clean-install